Identity Theft (part 2)

This is the second part to my article on identity theft and credentials – the first part is here:
Identity Theft (part 1) | Smart Thinking Solutions
If you have read that you know I am going to start with how!
How did the Snowflake the breach happen?
The whole attack started with an infection of info-stealing malware on the company’s systems dating back to 2020. This malware exfiltrated a variety of information and among it were credentials that were not protected by MFA – which was not turned on by default.
“[Snowflake] said it appeared hackers had used login information to access a demo account owned by a former Snowflake employee.” (BBC News 1, 2024)
These credentials gave access to the system and the threat actors simply logged in and ran some basic utilities to gather account details and then escalated the SQL commands across the network to exfiltrate customer account details. (Push Security (2025))
The whole attack hinged on a malware infection and unmanaged credentials with sufficient privileges to allow them to cause chaos.
Your Takeaway
So you do not hold data on 560 million clients (BBC News 2, 2024), but you do have information that either legally you have to protect under UK law (The UK GDPR, 2025.) and organisational data on your operations which I am sure both you and other stakeholders would prefer was confidential but there are takeaways for everyone from the Snowflake Attack.
Credentials are everything when considering identity theft.
When issuing a set of credentials to one of team, for Microsoft 365, the bank, your accounting system etc., do you take a moment and consider what trust you have put in that person? Have you trained them of significance of any passwords and usernames you provide them with to do their work and the cyber security consequences if they are compromised?
Identity Theft Mitigation
To finish here are some “good practice” pointers for you to think about:
- Enforce MFA but provide training on the ways this can bypassed.
- Have a password policy that is easy for the user to understand but also effective.
- In your cyber security awareness training include a section on the threat that reusing passwords poses to your organisation.
- Saving passwords in (some) browsers is not an issue but have a policy to manage it.
- Employ the “Principle of Least Privilege” – to every employee, including all those on the board and owner managers.
Manage Identity Cyber Security
You need a policy in place – which is used and obeyed to manage credentials and identity in your organisation – it should look something like this:
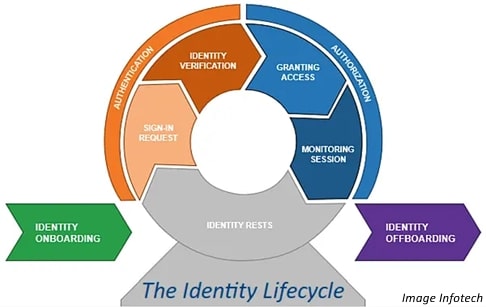
Next…
Cyber Security Theatre – get your tickets now!
Clive Catton MSc (Cyber Security) – by-line and other articles
References
Push Security. (2025). 2024: A year of identity attacks. Retrieved March 1, 2025. https://pushsecurity.com/.
The UK GDPR. (2025). Information Commissioner’s Office. https://ico.org.uk/for-organisations/data-protection-and-the-eu/data-protection-and-the-eu-in-detail/the-uk-gdpr/
BBC News. 1 (2024, May 31). All Santander staff and millions of customers have data hacked. https://www.bbc.co.uk/news/articles/c6ppv06e3n8o.amp
BBC News. 2 (2024, June 1). Ticketmaster confirms data hack. https://www.bbc.co.uk/news/articles/cw99ql0239wo
Further Reading
Photo by James Sutton

