Back to Basics Your Password the Finale

In part 4 of this password mini-series, we took a short detour into how passwords and identity can be compromised within your trusted organisation. Today we are going back to the ways users compromise their own passwords and how hackers know this and so exploit it when it comes to brute force hacking attacks. (Have a look at one of my previous articles in this series to find out about brute force attacks.)
Password Re-use
For this final part of the series, I want to look at one of the most regularly exploited password flaws – re-using passwords (Bowen. 2020). You can create a password that meets all the requirements your organisation lays out for a secure password and pass, but if you then choose to use that great password for several different services, social media, dating sites, online shopping etc., it only takes one of those services to be compromised or for you to fall a victim of a phishing attack where you reveal this great password by mistake and you have compromised not only your work systems but personal accounts as well. As soon as the threat actors gain one set of working credentials, their automated hacking tools go off and try them against as many other services as possible, just in case you are one of the 65% (Bowen. 2020) who reuse passwords. At 65% it is worth the hackers trying.
Password Reuse Mitigation
I could go on to explaining how multi-factor authentication can help defend against these types of credential-stuffing attacks, but I won’t. This article is about you NOT RE-USING PASSWORDS, finish.
Passwords and Your Organisation
It is quite simple, write a password policy – the National Cyber Security Centre (NCSC) has a page explaining what the minimum password requirements should be – there are links below. I have included a slide from our Cyber Security Awareness Training on what a great password is.
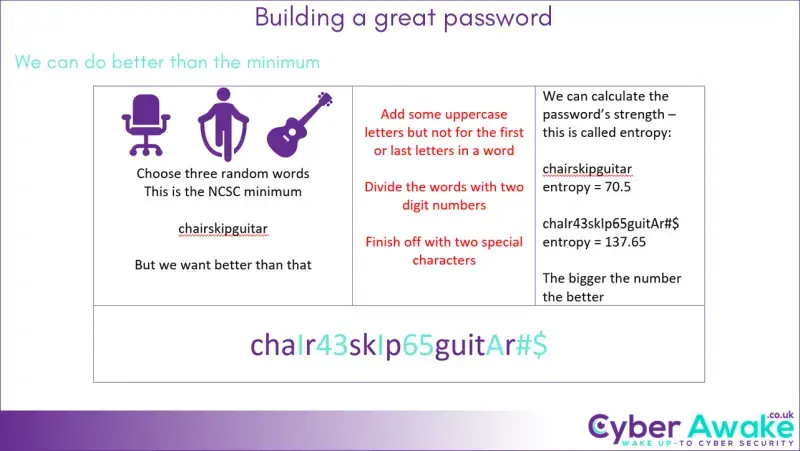
Something that has developed recently here in the office, is that we are requiring the special characters not to be at the beginning or end of the password.
Once you have written the policy, circulate it with links to these five short articles I have written so your team knows how important it is for good password discipline.
Just one more thing…
Our online training is more than just passwords – you should sign up for that as well.
Clive Catton MSc (Cyber Security) – by-line and other articles
References
Bowen, K. (2020). Your employees are reusing passwords – find out how many. Infosecurity Magazine. https://www.infosecurity-magazine.com/blogs/your-employees-reusing-passwords/
Further Reading
Move away from text- or voice-based multi-factor authentication
Back to Basics – The Password
Back to Basics – The Password Part 2
Back to Basics – The Password Keyboard Walk Part 3
Back to Basics – Password Sharing Part 4
From the National Cyber Security Centre:
Three random words – NCSC.GOV.UK
Using passwords to protect your devices and data (ncsc.gov.uk)
Photo by Ann H


