Passwords – Back to Basics
The summer is coming to an end and most businesses treat this as an opportunity to start something new – however I am going to start with something old – passwords.
…pssst. I have a secret. What’s the password?
Passwords have been around forever. In the Bible the password was “shibboleth”, the Romans had “watchwords”, “tessera” is Latin for password and who could forget “Open Sesame”. In our connected, digital world we all depend on them and have depended on them since Professor Fernando Corbato started using them to share resources on the MIT computer in 1961. (Wikimedia Foundation. 2023)
There are better options available such as passwordless systems using an app on your phone, but not every service has updated to this yet.
This article is not about creating a “secure” password, for that look here.
When it comes down to it breaking a password is all about guesswork – very fast guesswork by powerful computers. You do not want to make it easy for the threat actors to quickly guess your secret password.
We all have to live with passwords, so let’s have a look at the password mistakes users make that threat actors love.
Passwords – It’s all about the core
Most users start a password using a common core – which is rarely random – it usually has some attachment to the user or is related to their role at the company so they can remember it. They then increment this core for compulsory password changes or when choosing a new password for another service.
The hackers know this so their “try-me” password lists (called a dictionary attack) include the most common core words: “password”, “admin” and even the infamous p@ssw0rd, and Liverpool (insert your own sports team), among many others (Specops. 2023).
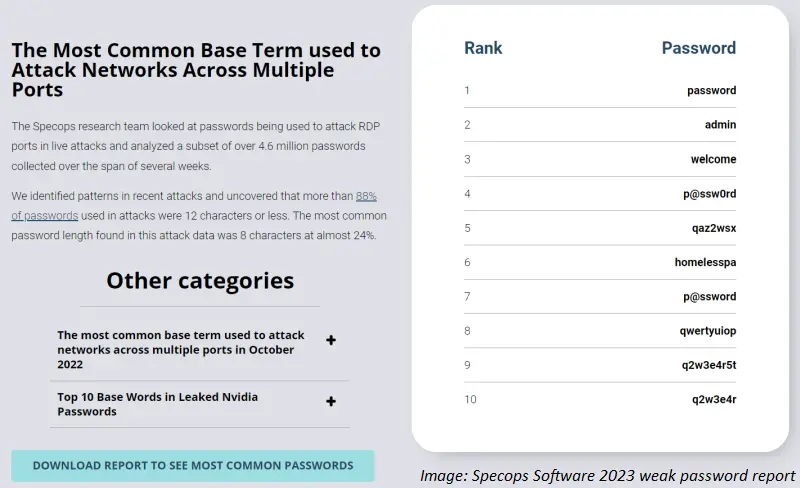
Other things people repeat that can be factored into a hacker’s password list is a capital letter at the beginning of words and a symbol at the end.
Significant Others and Your Passwords
Do not think by choosing the name of your partner, child, cat, car, favourite holiday destination, Mother’s maiden name, etc., etc., etc., you will be better off. It takes no time online for the hackers to find out these things about you.
Do not forget about the numbers
(update January 2024)
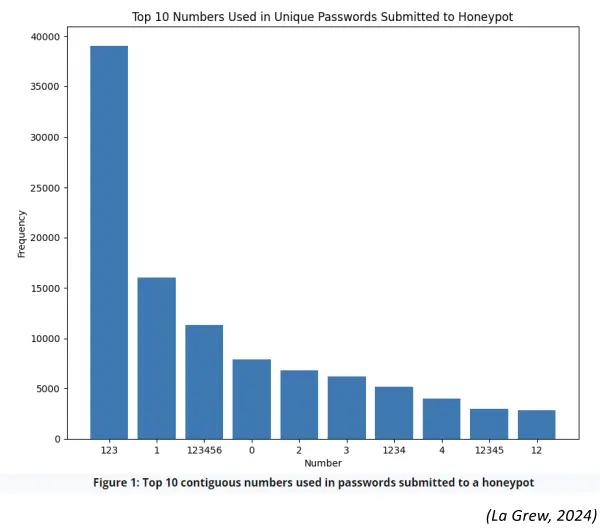
I have come back to this article after reading a short research article by Jesse La Grew in which he examined the number combinations people include in their passwords to make them more complicated. Again it seems people are people and these are as predictable as 123! (La Grew, 2024)
Your takeaways from today
Remember that the threat actors only need to crack the weakest password in use in your organisation. Training is essential.
Try to be really random with your passwords.
Next
More about passwords…
Clive Catton MSc (Cyber Security) – by-line and other articles
References
Wikimedia Foundation. (2023). Fernando J. Corbató. Wikipedia. https://en.wikipedia.org/wiki/Fernando_J._Corbat%C3%B3
Specops. (2023). Specops Software 2023 weak password report. Specops Software. https://specopssoft.com/our-resources/most-common-passwords/
Further Reading – Passwords
Something better than a password – passwordless Authentication
Because It’s Friday – Two Password Stories


