It All Starts with a Phishing Email

You do not have to take my word that a serious cyber-attack can start with a phishing email, just about every year since it has been produced the UK Government’s Cyber Security Breaches Survey has consistently recorded that phishing emails are among the most recorded cyber attack and lead to the many incidents (UK Government, 2023). Even the most sophisticated of cyber attacks are often initiated with a phishing email. An email is an easy way into any organisation that can lead on to an expensive incident (Chen & Magramo, 2024).
Phishing Email in the Real World
I have written about several real-world phishing email attacks recently (links below), including just yesterday on Smart Thinking, these were examples taken from my Inbox and Apple Watch. Today’s examples are from our CEO’s Inbox.
The Top of the Management Tree
The managers with responsibility in any organisation, large or small, are prime targets for the threat actors as these are the people who can give the most profit to the hackers if compromised – it is called Whale Phishing (NCSC, 2020). They are also the people who are likely to skip the cyber awareness training as they will be too busy or better still they have made the decision that cyber security awareness training is too expensive and so have not bothered to have their teams trained.
Whale Phishing Email
Here are two emails our CEO received:
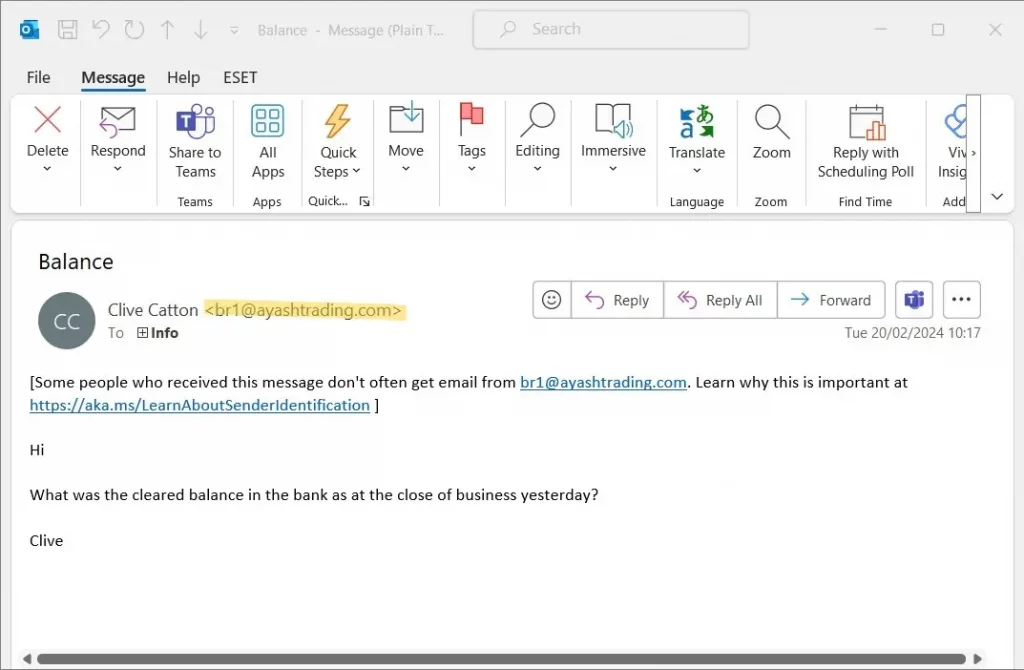
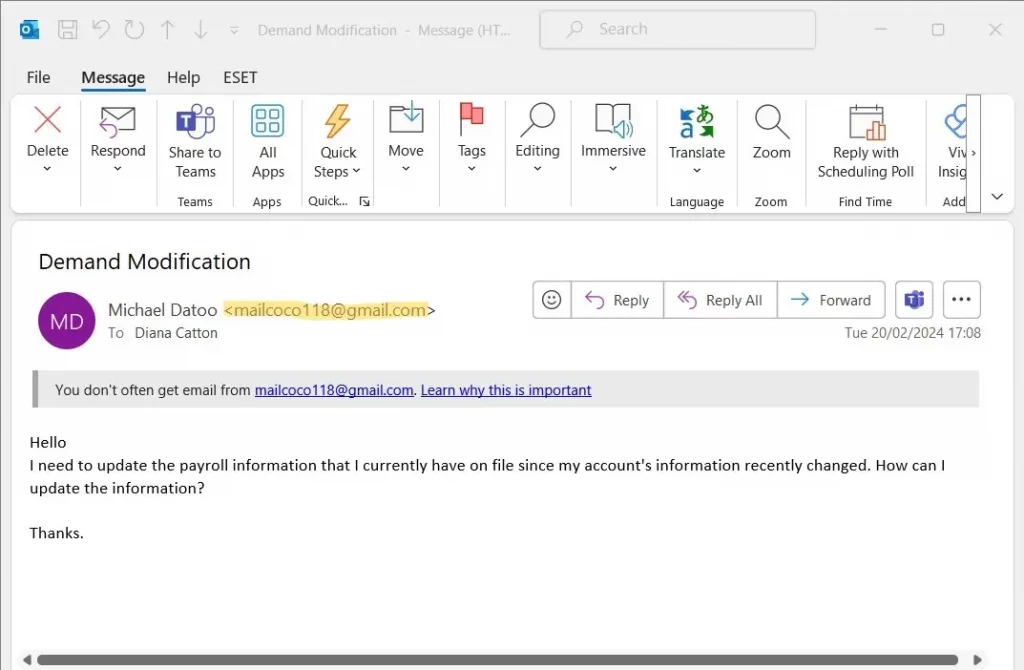
Now these are not very sophisticated, the messages are simple and there are obvious errors in the email addresses so they are not likely to work anywhere. But that aside if they were better crafted we still have “email disconnected” procedures in place that would disrupt these types of financial phishing email attacks.
What now?
You need to ask yourself two questions:
- Do you have procedures in place to disrupt financial cyber-attacks?
- And what type of CEO, CFO or senior manager are you?
Next week
Phishing attacks and credentials.
Clive Catton MSc (Cyber Security) – by-line and other articles
Further Reading
Someone is Trying to Get In – A Real Email Phishing Attack | Smart Thinking Solutions
Bugged by Phishing Email Attacks | Smart Thinking Solutions
Bugged by Phishing Email Attacks (pt. 2) – CyberAwake
Whaling: how it works, and what your organisation can do… – NCSC.GOV.UK
References
Chen, H., & Magramo, K. (2024, February 4). Finance worker pays out $25 million after video call with Deepfake “chief financial officer.” CNN. https://edition.cnn.com/2024/02/04/asia/deepfake-cfo-scam-hong-kong-intl-hnk/index.html
NCSC (2020) Whaling: How it works, and what your organisation can do about it, NCSC. Available at: https://www.ncsc.gov.uk/guidance/whaling-how-it-works-and-what-your-organisation-can-do-about-it
UK Government. (2023). Cyber security breaches survey 2023. GOV.UK. https://www.gov.uk/government/statistics/cyber-security-breaches-survey-2023/cyber-security-breaches-survey-2023
Photo by Johannes Plenio


