Anti-virus – This is why you need more and better…

We are all using industry-standard anti-virus – well at least most of us are, a penny-pinching client we have just got rid of thought the free version of AVG was good enough. Let’s get this straight, AVG is a good product. The free version does work. However, it is not enough protection for a modern business on the internet.
But the threat actors know we all use effective anti-virus so they are always looking for new ways to subvert your anti-virus protection. They could be slipping the malware to you past your anti-virus, obfuscated in a .bat file (Mertens. 2023a) or buried in an image using steganography (Mertens. 2023b), or whatever new way the hackers dream up for tomorrow.
Nothing there for your anti-virus to detect!
You could get a phishing email that gets past your anti-virus because there is nothing there to detect in the first place, like this one I got from the manager of the Swansea University procurement department:
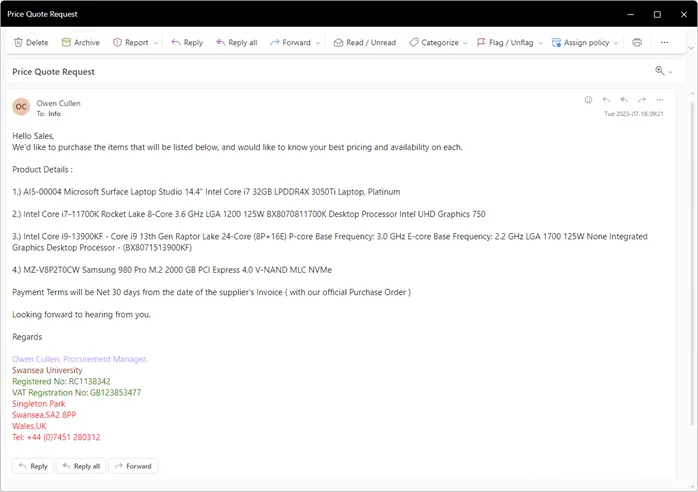
Now I am sure this email would not really fool anyone – for a start Owen Cullen’s email address is showing as “swanseaprocurement022@gmail.com” not a very likely email address for someone acting in an official capacity at a major university. It must have been a slow day at the office – and I was looking for my next CyberAwake article – so I reached out to Owen to inform him about the phishing attack that was using his name in vain, just to see what the response was.
I rapidly got a reply from a member of his department, apologising and explaining that there were several attacks doing the rounds using Swansea University staff names. I also got an automated email – probably generated by emailing anyone in the procurement department – because when I replied to the nice email, I got another explaining the purchasing process for Swansea University.
Swansea University did nothing to encourage this attack – Owen’s details are found easily on the University’s own site – I found them – and the automated email explaining the procurement process protects any victim that does the basics of due diligence before entering into a commercial arrangement.
So what if my anti-virus missed this, it is not much of a threat!
I agree. For this attack to succeed the victim would have to get into an email exchange with the attacker, ignoring the obviously bogus email address, and then dispatch the required equipment, to a stranger, without payment!
But what happens if your member of staff is offered a BMW in an email that slips past your anti-virus? (Toulas. 2023) This is a technique that is being used successfully by Russian hackers on diplomats in Ukraine – probably the most “cyber aware” nation on Earth at the moment.
Add Cyber Security Awareness Training to your cyber security arsenal.
Clive Catton MSc (Cyber Security) – by-line and other articles
One last thing…
When I told the person who reached out to me that I was going to write about this email in one of my blogs, I was told I would have to clear that with Swansea University’s PR and Marketing Team. I didn’t but I did get another automated email explaining the University’s procurement policy.
Just one more thing…
Diana will be concluding the risk series over the next two weeks.
References
Mertens, X. (2023a). Deobfuscation of malware delivered through a .bat file. SANS Internet Storm Center. https://isc.sans.edu/diary/Deobfuscation+of+Malware+Delivered+Through+a+bat+File/30048
Mertens, X. (2023b). ShellCode Hidden with Steganography. SANS Internet Storm Center. https://isc.sans.edu/diary/ShellCode+Hidden+with+Steganography/30074
Toulas, B. (2023). Russian state hackers lure western diplomats with BMW Car ads. BleepingComputer. https://www.bleepingcomputer.com/news/security/russian-state-hackers-lure-western-diplomats-with-bmw-car-ads/
Further Reading
Why I do not like “Meet the Team” web pages – CyberAwake
Featured Photo by Lum3n


