Pull the Plug: But I haven’t got a plug!

This article is a response to a question I got about this article “Minimise the Damage – Planning and Preparation”.
Ransomware Incident Response
In my article looking at the immediate response any individual or organisation should make if they even suspect malware is running on their machine I suggested that suspect machines should be isolated straight away – before even notifying IT or Cyber Security support. It makes sense – the quicker an infected machine can be disconnected from your network, the internet and your cloud storage, the quicker you can start to limit the impact of the (ransomware) malware.
Pulling the cable is easy – if you know where it is?
Now to technical people it seems easy when you say “isolate the computer”, they will go looking for the network cable plugged into the back of their desktop, side of their laptop or even the laptop docking station or USB hub. I have found even non-technical people can be quickly taught how to isolate in this way, even though most do not like scrabbling behind tower computers, down on the floor in the dust!
The Wi-Fi Question
When it comes to Wi-Fi connections things can get a bit more difficult – the options can start to mount up here and users seem more reluctant to switch the Wi-Fi off. Some laptops turn off the Wi-Fi with a physical switch (not so common on modern machines), or a keyboard function switch (the office laptops we supply clients have this option) or you have to use the Windows Task Bar Wi-Fi Controls and access either the Wi-Fi or Airplane mode – see fig.1. I usually demonstrate the last method as it covers the most users.
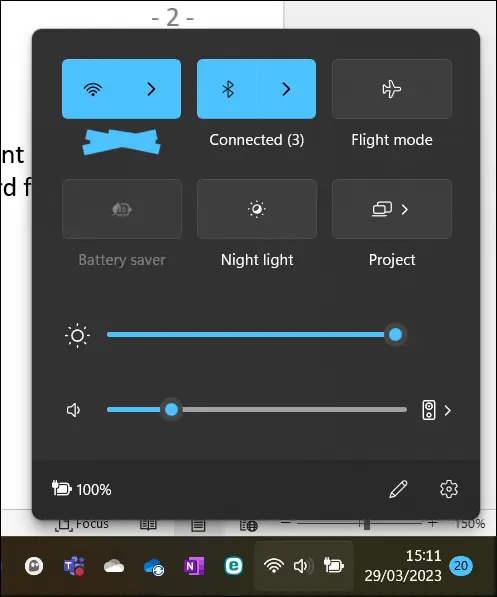
Another place to isolate your network
Then when I was working on an incident response plan for a client we came up with another way of isolating infected machines quickly – switching off their router modem (fig. 2). It was a small office and all the wired and wireless devices ran though a single Draytek router modem that was easily accessed by anyone in the office and a prompt card fixed to the wall reminded people what to do when they were stressed.
I have scaled this response to larger offices.
One thing to note is that the incident response plan then outlines how the router modem and network are brought back online.

Training rules OK!
If malware strikes then getting the infected device isolated quickly is important and it all comes down to having an incident response plan and training. (UK Government. 2022). We can help with both of those.
Clive Catton MSc (Cyber Security) – by-line and other articles
I will be taking a break for the Easter holidays and will be back on 13 April 2023.
References
NCSC. (2021). Mitigating malware and ransomware attacks. NCSC. Retrieved March 29, 2023, from https://www.ncsc.gov.uk/guidance/mitigating-malware-and-ransomware-attacks#stepsifinfected
UK Government. (2022). Cyber Security Breaches Survey 2022. Retrieved 20 March, 2023, from https://www.gov.uk/government/statistics/cyber-security-breaches-survey-2022/cyber-security-breaches-survey-2022
Further Reading
Ransomware – A Primer – CyberAwake
Photos by www.clivecatton.co.uk


