Ransomware – The Impact

The Impact of Ransomware
So the worst has happened. You come into work on a Monday morning early, to get a head start on the week. You switch on your PC and whilst it is booting you make a coffee. Now you sit down and go to open Outlook to check your schedule for the week, but you have a message on your screen. Ransomware!
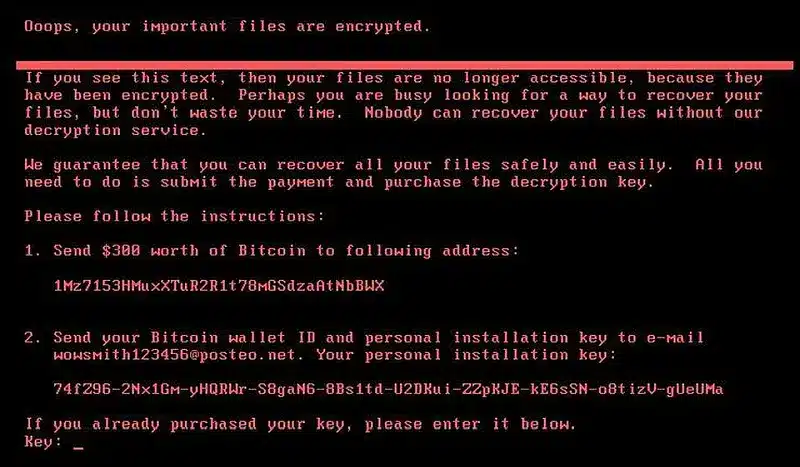
What now?
The complete answer is beyond the scope of this article. But you should have a plan in place to deal with this eventuality. What I plan to do today is look briefly at some of the areas that will be affected by ransomware malware, just to check you have them covered in your plan.
Disruption to your operations
Whether you make widgets or supply services, if you and your team are denied access to your files and information, then getting any work done will be problematical. Add to that, the ransomware needs to be dealt with and you will need something in your plan for business continuity.
Setting up a secondary factory is a challenge.
Setting up a secondary office can be easier, switching to working on a smartphone or tablet is practical in the short term – but before that can happen someone has to check what data has been impacted and where the malware has spread to – so no using laptops that have been connected to an infected network (yet). We, for example, have an agreement to use another company’s training room or boardroom should the worst happen to us.
After the event there will be an impact on production due to new procedures and training for your team.
How far has the ransomware Penertrated?
You will need a plan for checking your endpoints, networks and storage for the malware and the extent of the encryption. We always start with a clean version of ESET brought in on a USB stick from a clean network – although there can be issues using a USB stick.
Communications
Does your plan include a set of template documents that you prepared when you were not under pressure, custom written for all the stakeholders that you need to make aware of issues you are having. This can include suppliers who will not now be able to deliver to you today, customers who are relying on a visit today or deliveries you need to make. Your business will have its own unique set of stakeholders and emails.
Do some of those stakeholders deserve a phone call? If so, better get the CEO to make those calls as the production and technical teams are working on the problem. Is there a script for the CEO?
One more point about communications. Do you have a plan for if your email server is not working? We do.
Then there is the Information Commissioner’s Office
Your investigations may reveal that you need to notify the Information Commissioner’s Office about the compromise of personal data (ICO. 2018). Does your plan describe what circumstances will trigger this? Do you have a plan for collating the information that will be passed onto them?
… and the Police
Remember criminals are demanding a ransom from you. That is a criminal offence. Should you call the police? Do you need to call your lawyer?
You could find that one of your team was involved. Do you have procedures if you need to remove one (or more) of your team from site and bar them from your systems?
Reputational harm
How you deal with the situation will have a bearing on the amount of reputational harm that your organisation will suffer. Good, and I have to say it, honest communications may seem difficult at first but news items that highlight when cover-ups have been revealed will do far more damage and keep you in the news longer. (Martin. 2023)
Speaking of the media, do you have a spokesperson, briefed and ready, if it gets that far?
If your factory or warehouse is at a standstill, then your business continuity and incident response plans will need to have the budget to get the systems flushed of ransomware, then back up and running as soon as possible to resume supplying widgets to your customers.
Back-ups
Whilst looking at the ransomware message – way back at the beginning of this article – you should have had one small glimmer of relief, you know you have a complete ransomware resilient back-up.
Next
More on those back-ups and other consequences of ransomware.
Clive Catton MSc (Cyber Security) – by-line and other articles
References
Grimes, R. A. (2021). Ransomware protection playbook. John Wiley & Sons, Incorporated.
ICO. (2018). UK GDPR Data Breach Reporting (DPA 2018). Information Commissioner’s Office. Retrieved February 15, 2023, from https://ico.org.uk/for-organisations/report-a-breach/personal-data-breach/
Martin, A. (2023). British government minister told council to keep quiet after ransomware attack. The Record from Recorded Future News. Retrieved February 15, 2023, from https://therecord.media/british-government-minister-told-council-to-keep-quiet-after-ransomware-attack/
Further Reading
If you must use portable USB drives, then you must read this…
Ransomware Mini-Series (2023)
This is part 6 of my ransomware mini-series:
Ransomware: Is it a Threat? (Part 1)
A Bag of Spanners – Planning and Preparation (Part 2)
Minimise the Damage – Planning and Preparation (Part 3)
Detecting Ransomware (Part 4)
Ransomware – What Not To Do! (Part 5)


