The Blame Game

I finished my last CyberAwake article with the following paragraph about blame:
Just don’t blame your people if they click on a link – get them to report it so steps can be taken to limit the damage. There is a link between blame and the amount of damage a cyber incident will cause.
Don’t Blame your Team – “Just Click Here” – January 2023
Today I’d like to look at that statement a little more.
When something goes wrong – who do you blame?
It is very difficult when something goes wrong in your business not to want to blame someone – it is human nature. However if that situation has adverse consequences for the organisation it is important to know how it happened – if you do not know how things went wrong then how do you stop it happening again? All very business 101. But if the consequence is that all the company data is encrypted, your operation cannot function – the publicity is bad and criminals are demanding a lot of money to unencrypt the data and not publish it on the internet. In those circumstances expecting a staff member to come forward and say “I did it” is unrealistic.
But for good Cyber Security we need quick owning up not blame
When someone clicks on a malicious link and either gives away their credentials or activates malware on their computer the quicker the IT and cyber security support finds out about it, the quicker the damage can be limited and fixes put in place. Remembering of course that malware, especially ransomware, will operate in stealth mode so even if nothing appeared to happen when you let that Word macro run, it is still a good idea to report it.
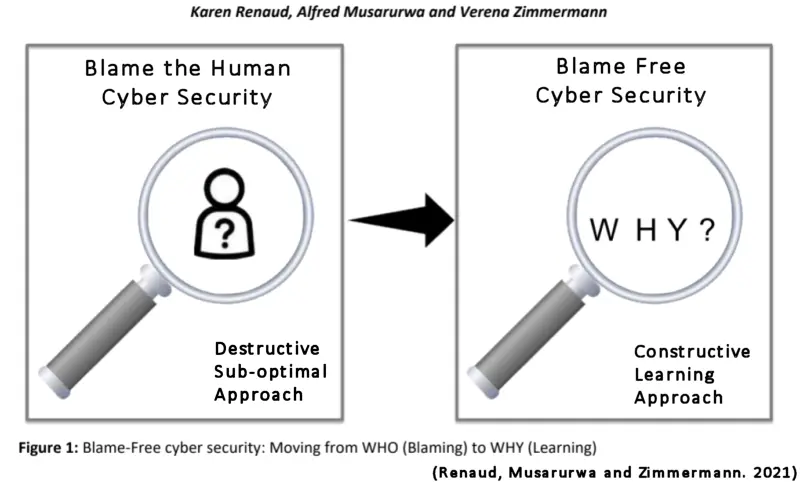
The paper by Renaud, Musarurwa and Zimmermann discusses this subject in depth looking at why organisations blame and what impact it can have on their cyber security – spoiler alert, it is only bad.
One side consequence of “blame and punishment” is that valued members of your team will feel they need to move on to other jobs to get out of a bad atmosphere. We have had to deal with both types of company and being confronted by an angry CEO, who demands to know who did it, does not put our support team in a good frame of mind to get down and fix the problems. They like the approach where they get a cup of tea and a chance to discuss what happened with a trusted member of staff, who has disconnected their infected computer from the company network.
Have a read of the paper – it is publicily available through Google Scholar – as it makes interesting reading – and if you run a blame culture it will make uncomfortable reading.
Creating a cyber security culture, where it is “us against the hackers” is really the only way forward.
My closing words…
Blame and hunting down the culprits of unintentional breaches of cyber security plays right into the hands of the threat actors – don’t do it.
Clive Catton MSc (Cyber Security) – by-line and other articles
References
Renaud, K., Musarurwa, A., & Zimmermann, V. (2021). Contemplating blame in cyber security. In ICCWS 2021 16th International Conference on Cyber Warfare and Security (pp. 309-317). Academic Conferences Limited.


