How much are you relying on your web designer to protect your reputation?

In my last article we looked at why you need policies in place to check what apps your team members are using across their devices – and I illustrated the risks with references to current software vulnerabilities and cyber-attacks. Today we are going to extend that discussion to include your website. (I am going to use WordPress as an example here of a web developer platform – your designer may use something else but the same principles will apply).
Your WordPress website security
Your website is your shop window to the world – it may or may not collect personally identifiable and/or sensitive information, you may have an online shop but whatever your site does it carries your reputation. Which means you should know what is going on with it. Your good cyber security due diligence will protect that reputation.
- Do you know the platform your website is based on?
I am going to briefly cover some of the most important cyber security steps you should be taking.
Who works on your website?
Most companies get a web developer in to build and manage their websites – perfectly fine, but it is still your domain and your website. One of the things I always check for clients is whether the web designer is using “in house staff”, known/identifiable contractors or “gig” contractors from the web. There is no wrong answer here, only wrong ways that they manage those people. All staff should be verified, after all they will be having access to your asset. (Kommineni and Parvathi, 2013)
- Who has access to the PII and/or financial details and data?
WordPress Updates, Back-ups and Plugins
This is all a question of software and from the previous article you now understand that software always has flaws which need fixing. As your website (software) is online, serious security vulnerabilities need patching quickly so the threat actors cannot exploit them – and if they do, that is where the back-up comes in. (Gall, 2022 and Williams, Tadlock and Jacoby, 2020 and Lindén, 2019)
- How do the web developers verify the plug-ins they use?
- Do they back-up your site? Where are the back-ups kept? How often is the back-up? Do they back-up before committing major changes?
- WordPress and the plugins will all need to be updated and patched during the life of the website. How?
Protect the administrator account
This is probably the most important task I will be discussing today. You should know who has administrator access to your website and what steps are in place to control that access. (Lindén, 2019)
- Multi-factor authentication (MFA) is a must – but see here for an exception we must manage.
- Make full use of the different levels of user – not everyone needs to be a global administrator
- Can you lock a user to a particular IP?
An essential layer of protection
Forty-three percent of the web is built on WordPress (WordPress, 2022) and so the threat actors have taken the time to find out the easy exploits. That starts with the login – which is usually access from the URL https://your_domain/wp-login.php, now every threat actor knows the front door to the site – making WordPress sites prime targets for brute force and credential stuffing attacks. (Lindén, 2019)
- I have already mentioned MFA
- Limit the number of incorrect logins and enforce lock outs
Here is an example of login protection in action, on one of the sites we manage for a client:
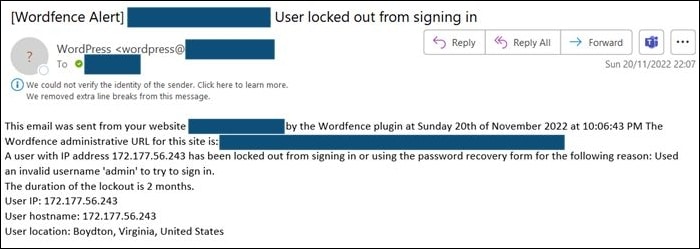
As you can see this threat actor used the obvious username “admin” which this client does not use. Obvious really – don’t use administrator or editor either.
We get hundreds of these types of email from across the websites we manage, the reason I chose this one is that the population of Boydton as reported by Google is 298.
Tempting as it is to go there and knock on all the doors and ask if the hacker lives there, I expect the real hacker was using a VPN, or using some other way to obfuscate their location, or there is a PC in the town infected with bot malware…
This is not the whole plan…
In an article that I want to educate you not bore you, I cannot cover all the points but hopefully this will get you thinking, acting or talking to me.
Clive Catton MSc (Cyber Security) – by-line and other articles
References
Gall, R. (2022, September). PSA: Zero-day vulnerability in WPGATEWAY actively exploited in the wild. Wordfence. Retrieved November 22, 2022, from https://www.wordfence.com/blog/2022/09/psa-zero-day-vulnerability-in-wpgateway-actively-exploited-in-the-wild/
Kommineni, M., & Parvathi, R. (2013). Risk Analysis for Exploring the Opportunities in Cloud Outsourcing.
Lindén, T. (2019). Building a secure WordPress website with plugins.
Williams, B., Tadlock, J., & Jacoby, J. J. (2020). Professional WordPress Plugin Development. John Wiley & Sons.
WordPress. (2022). Fast, secure managed WordPress hosting. WordPress.com. Retrieved November 23, 2022, from https://wordpress.com/


